Nutanix Flow is Nutanix’s Software Defined Networking (SDN) product filling a gap in its portfolio. One of the features is Microsegmentation based on flexible security rules. Read myblog post Enable Nutanix Flow to learn more about the product.
Nutanix Flow policy – Isolation
Isolation policies (as policy names state itself) restrict two defined groups of VMs from communicating with each other.
Use case
- Isolate DEV environment from TEST or TEST from Pre-PROD or Pre-PROD from PROD.
- VDI deployments where you can separate different VDI pools by isolation policy.
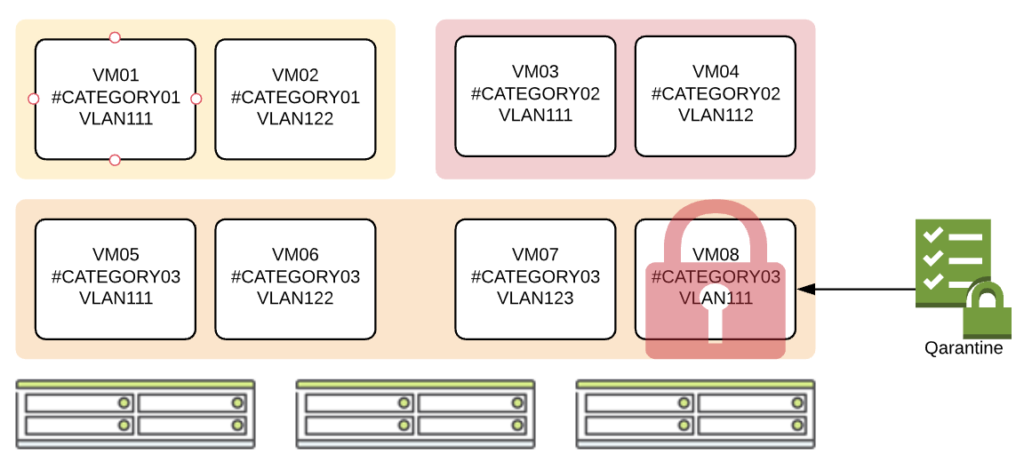
On below example VMs from #CATEGORY01 are isolated from 3CATEGORY02 VMs. However, VM’s from #CATEGORY03 can communicate to VM’s from other categories without any restryctions.
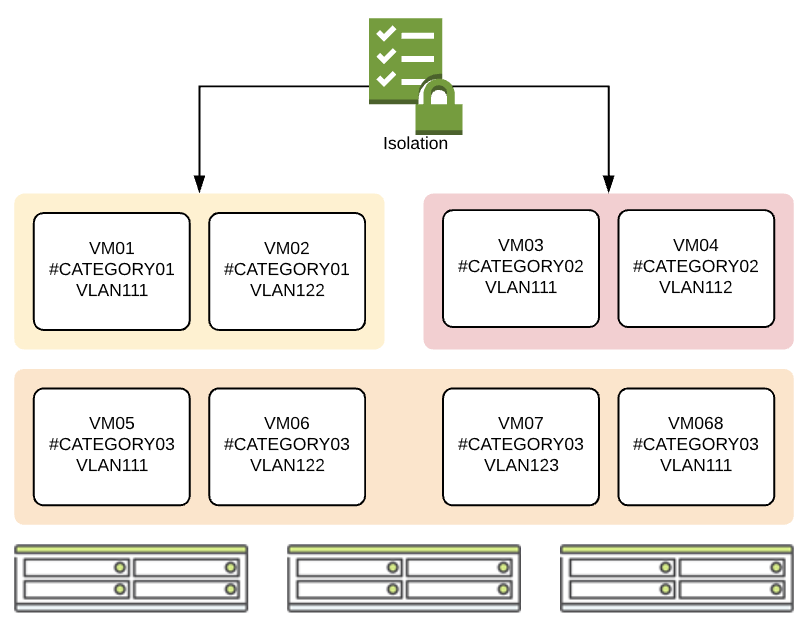
Security policies – Isolation
Nutanix Flow policy – Application
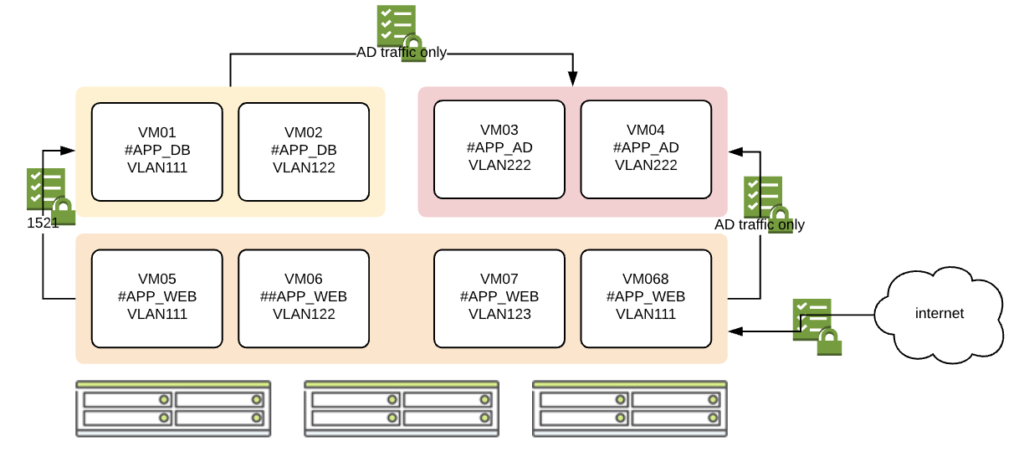
Application security policy is defining inbound traffic sources and outbound destinations for single or multi-tiered application. Using application policy we can define what are outbound and inbound traffic ports that application can use to communicate between its components.
On below example:
- Applications from #APP_DB and #APP_WEB can communicate to #APP_AD application over only Active Directory ports
- Application #APP_WEB can communicate to #APP_DB over 1521 port only
- Application #APP_WEB can communicate out to internet
Application fencing
Use case.
- Multi tier applications:
- database server
- application server
- webserver
- communication between applications from different security zones
Nutanix Flow policy – Quarantine
Quarantine policy is a programmatic or manual restriction of network connections applicable to single VM or multiple applications.
Use case
- Infected (by virus or malware) VDI desktop or desktop pool
In below example, on VM08 was applied qarantine policy to cut VM off the network. Virtual Machine keeps running (without any network connectivity) and it is available for inspection (via Remote console from Prism)
Quarantine Policy
Policy evaluation order
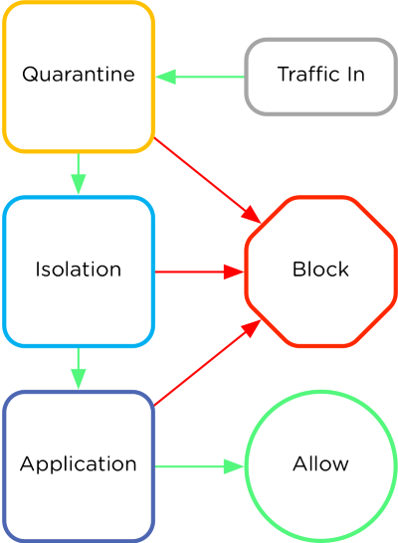
Incoming traffic is inspected in below order:
- Quarantine – the most strict rule
- Isolation
- Application
The order showed on the picture below give administrator flexibility where rules can be used together like application, isolation, and quarantine.
Source: Nutanix: Nutanix Flow – policy evaluation order